Data security is of paramount importance because of the ever-increasing risk of cyber attacks, supply chain attacks as well as AI threats. The global average cost of a data breach reached an all-time high of $4.45 million in 2023, as per the Cost of a Data Breach Report shared by IBM Security. In this blog, we’ll explore the main ERP security strategies and various issues of protecting data that apply to most industries.
Data Threats and Benefits for Maintaining Data Security
Data threats and benefits of maintaining data security. Here is an overview of the data security domain, along with the benefits of strong data security systems, detect the types of data that require protection, and outline the major threats that are faced by companies.
What is Data Security?
Effective data protection measures involve the implementation of real-time monitoring and immediately reacting to suspicious activities to ensure the safety of your data to fraudulent activity. Why is data security so important that regulators and authorities constantly create new data security guidelines and requirements?

Major Benefits of Robust Data Security
Here are some of the major benefits of high-level ERP security in your company –
- Data Protection
Being assured that your data is protected from internal as well as external threats can help to focus on your strategies in a better way than being worried about data breaches.
- Comply With Data Security Requirements
Implementing data protection and security best practices can help you ensure compliance with data security requirements. It will help your company to avoid hefty fines due to non-compliance.
- Enhance Your Reputation
Companies that are often looking for long-term cooperation always check the reputation of their potential partners. Applying reliable security measures for data protection also helps to gain the trust of customers.
- Minimize Litigation Expenses
Preventing a problem from occurring is always a wise way to remain cost-efficient rather than deal with the consequences. The greater the time and effort you spend on data security, the less money you’ll be spending on resolving and recovering from such a potential incident.
- Improve Business Continuity
Strong data security and privacy practices help to ensure uninterrupted operations, minimizing the risk of business disruptions, and loss of revenue.
What type of data requires the most protection?
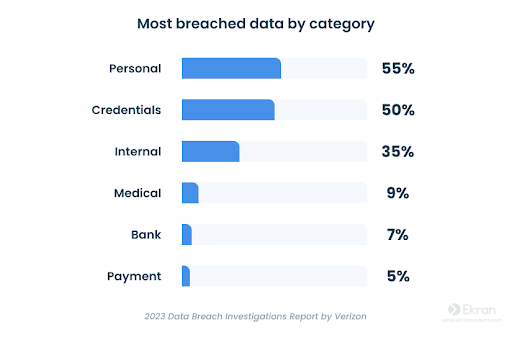
To understand what type of data is at risk, let’s find out the various types of data that are most stolen-
Your organization’s sensitive data needs to be guarded as per the relevant laws and regulations of your industry and jurisdiction. Additional IT standards that you need to focus on include NIST 800-53, NIST 800-171, and ISO 27000 Series.
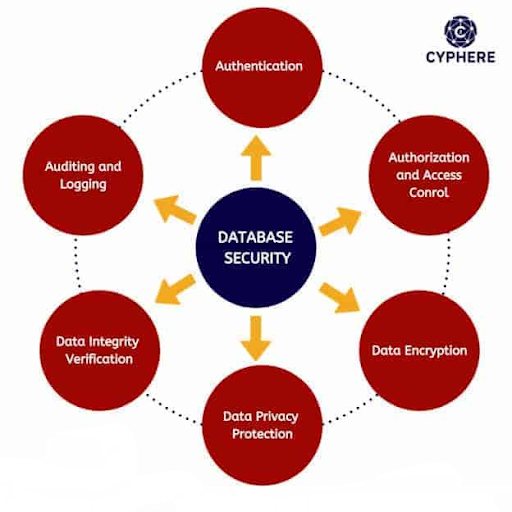
4 Major Threats to Corporate Data
No system is completely immune to cyber threats, insider threats, and misconfiguration. An organization’s sensitive data can be lost, damaged, or get into the hands of people with bad intent. Internal human threats, like external attacks, are usually caused by the actions of employees. 74% of all data breaches have a human element, as per the 2023 Data Breaches Investigations Record by Verizon.
To have a clear understanding of how data gets compromised, here are some examples of data breaches caused by insiders:
- Human Error and Negligence
A legitimate user can make mistakes because of negligence, lack of focus, fatigue, and other human factors related to cybersecurity. In January 2023, malicious individuals tricked a Mailchimp employee into sharing the company’s login credentials via a social engineering attack. So, at least 133 Mailchimp user accounts were compromised. Some others were the ones of famous companies such as Statista, Yuga Labs, WooCommerce, FanDuel, and Solana Foundation.
- Privilege Misuse
Users with privileges often engage in various types of misuse of data handling or unethical handling. Employees may intentionally destroy, steal, or damage the data of a company for their benefit. In May 2022, a research scientist at Yahoo reportedly stole intellectual property of their AdLearn product after receiving a job from the company’s competitor, The Trade Desk. Yahoo claims that the incident compromised their valuable trade secrets while giving competitors an edge.
- Third-Party Threats
Data threats can be due to partners, vendors, and subcontractors who have access to your company’s sensitive data. Third parties can act as intermediaries for outside attackers, such as supply chain attacks.
In June 2023, Zellis, a payroll solutions provider running operations in Ireland and the UK, faced a data breach because of the exploitation of a zero-duty vulnerability in MOVEit, their vendor. Several Zellis customers were affected by this breach, including Boots, Aer Lingus, British Airways, and BBC. Personal data of many of their employees were compromised.
- Malicious Insiders
Internal users might steal, damage, or destroy a company’s data for their personal gains. In August 2023, two former Tesla employees were blamed for leaking their personal data of Tesla’s existing and former employees to a newspaper based in Germany. Their actions led to the exposure of personal data of 75,735, causing Tesla a GDPR fine of $3.3 billion.
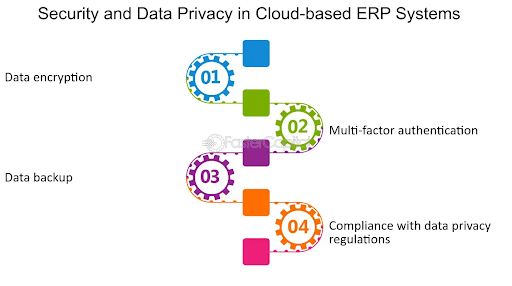
4 Ways to Secure the Erp Data of Your Organization
To answer this question, let’s have a look at the major ways to ensure ERP security. As per Gartner, the four major methods of data protection are-
- Encryption
It prevents unauthorized parties from reading the data of your company.
- Data Erasure
Data erasure involves cleaning your data repository which is no longer in use.
- Masking
Masking helps to anonymize or suppress high-value data by replacing sensitive information with random characters. It can also be utilized as a substitute data using a low-representative token. This method is known as tokenization.
- Data Resilience
Data resilience involves full, differential as well as incremental backups of important data. Storing valuable data across various locations makes it recoverable and safe from various cybersecurity threats.
What is Data Sensitivity?
There are primarily five parameters of data review-
- Knowledge about which data is sensitive
- Location where the sensitive data is stored
- Knowledge about who has data access
- Channels where the sensitive data goes
- How to monitor interactions with sensitive data
First and foremost, assess the sensitivity of your data. There are three data sensitivity levels-
- Confidentiality
Data is safe from unauthorized access.
- Integrity
Data is reliable and accurate, and sensitive information is secure from illegitimate changes.
- Availability can be easily accessed by all legitimate users.
To adhere to the three principles, businesses need realistic mechanisms called data security controls. These are countermeasures that are used for preventing, detecting, and responding to security risks threatening your important assets.
Source: FasterCapital
Major Data Security Best Practices for Your Organization
While various businesses, regions, and industries might require various data protection practices, we have selected the most effective practices that suit the needs of most organizations-
- Define the Sensitive Data
Consider reviewing your data by implementing the following security measures –
- Sensitivity
Which of the data you possess is sensitive?
- Location
Where the sensitive data gets stored.
- People
Who within the organization has access to which data?
- Channels
Where does your sensitive data go?
- Visibility
How to monitor interactions with sensitive data.
First, access the sensitivity of your data. There are primarily three data sensitivity levels –
- Low-sensitivity data
It is safe or used by the public, like for example general information published on websites.
- Medium-sensitivity data
It can be shared within your organization but not the public. There can be disastrous consequences because of a data leak.
- High-sensitivity data
This data can be shared within a small circle of insiders. If it gets destroyed or compromised, it will have a disastrous impact on the organization.
It’s also essential to ensure visibility into your data so that you can have clarity regarding the exact data which requires the highest level of protection.
2. Develop a Cybersecurity Policy
The second task is arranging all cybersecurity mechanisms, activities, and controls to form a working strategy. Ensure that your company’s human and technical resources effectively support your data security-related efforts by implementing a data security policy:
6 Tasks for Creating a Data Security Policy
- Develop a data usage policy
- Implement a risk-based approach to data
- Perform a database audit
- Implement patch management
- Restrict the employee termination process
- Appoint a data protection officer
Create rules related to the sensitive data of your organization regarding your data usage policy. It should contain guidelines for stakeholders, employees, and third parties while handling data. Execute a risk-based approach to data. Evaluate all the risks related to the use of data in your company with data weak points.
After that focus on the highest risks first. Regular database audits help you to understand the present situation and set clear goals for further data defense. They also enable you to track all user actions and view the detailed metadata at any time.
Execute a proper patch management strategy. Here is a list of steps and rules for patching the weak points within your corporate environment or just in code. Perform patches regularly and document all sections regularly. When you terminate employees, monitor and record their activities and operations with critical assets to revoke access rights fully.
Also, think about hiring a data protection officer (DPO) who will control compliance along with data security requirements offer suggestions on data protection measures, and handle security-related complaints from staff, providers, and customers. The DPO will also deal with issues like security failures. You can also follow examples of IT security policies to find the ideal ones for your organization.
3. Develop an Incident Response Plan
An incident response plan sets out actions for handling cybersecurity incidents and reduces their consequences on time. You can refer to HIPAA, NIST 800-53, PCI DSS, and other laws, regulations, and standards that set incident response requirements. Make sure to-
- Explain security incidents, their types, and the severity of their consequences on your company.
- Select people who will be in charge of handling such an incident.
- Perform a security audit, enhance your plan based on past incidents, and make a wide list of incidents your company may encounter.
- Develop a communication plan and list of authorities you should inform when such an incident occurs.
- Develop a data recovery plan to ensure that you can restore the data and systems quickly after an incident.
4. Provide Limited Access to Critical Storage
Protect data access points as your starting point efficiently.
3 Tasks for Proper Access Management
- Control physical access
- Execute password and identity management
- Apply the rule of least privilege
Physical access controls protect access to data servers via the locking and recycling of databases, video surveillance, various types of alarm systems, and network segregation. The ones that you use should also provide secure mobile device and laptop connections to servers, computers, and other devices.
Source: StealthLabs
5. Ensure Safe Data Storage
Before implementation of other data protection practices, ensure that the data is stored safely at various levels –
- Secure physical storage
- Enforce data-saving methods
- Manage all devices
Carefully store physician media that contains your data. It is essential to use storage devices that are waterproof and fireproof. Moreover, pay special attention to the way you secure your data using the latest technologies. We’ve already talked about backups, masking, encryption, and confirmed erasure as the major data security measures for the safe storage of your files.
Think about deploying USB device management tools to secure data stores in devices. Secure the information available on mobile devices and data shared through removable storage devices. Don’t overlook solutions that provide visibility and notifications related to suspicious activity on devices that contain sensitive data.
6. Periodically Monitor User Activity
Consider improving the visibility of your organization’s user User Activity Monitoring (UAM) solutions. Comprehensive real-time monitoring of all employees who possess access to sensitive information such as –
- Session recording with metadata
- Incident response features
- Automated notifications related to suspicious actions
The ability to view any user session linked to your sensitive data at any time and also receive alerts related to abnormal user activity can help you ensure safe interaction with the critical assets of your organization. By doing so, you will have a higher chance of avoiding a data breach.
7. Manage Third-Party-Related Risks
It’s essential to monitor the actions of third parties inside your company’s IT infrastructure. Third parties might include business partners, vendors, suppliers, and subcontractors apart from external users who have access to the critical systems. Even if you trust them, there are chances that their systems are vulnerable to hacking and supply chain attacks.
Apart from monitoring third-party vendor’s sessions on-premises and in the cloud, ensure that you clearly understand what your third-party landscape looks like and define workers who control and process your data. Sign a service-level agreement (SLA)with third-party service providers. Ask for daily accountability to ensure data security standards are maintained. Work with vendors to enhance your mutual security.
8. Educate Your Staff About Data Security Risks
It is essential to educate your staff on how your staff handle your corporate assets safely and how to recognize malware and social engineering attempts. Offer new training to offer updated information about the latest data threat scenarios. Consider offering introductory training to new employees. It’s essential to educate the staff and trainees on a regular basis about ERP security. Educate them about the following –
- Negligence and software
- Show security measures for each endpoint
- Ask the trainees for feedback
- Provide tips to prevent phishing attacks
- Teach them how to handle your data
As per the people-centric approach to data security, employees play a major role in the threat reduction process. Knowledge can considerably reduce people-related data leaks and make security measures more obvious to your staff.
9. Use Dedicated Data Security Software
Consider launching a specialized ERP security solution to ensure the safety of your sensitive data. While implementing security software, give precedence to solutions which have these capabilities –
- User activity monitoring
- Automated access management
- Notifications on security events
- Auditing and reporting
- Password management
Moreover, you need to ensure the visibility of different types of devices and endpoints from one place. Deploying too many solutions and tools may not always work since it may slow down your IT and security management processes, increase your expenses and make maintenance more complicated.
FAQs
1. Why is regular updating important for ERP security?
Regulating updating is essential for ERP security as it helps to make sure that the system is equipped with the newest patches and security enhancements. These updates often fix known weaknesses and boosts the system’s defenses against possible cyber threats.
2. How robust access controls ensure ERP security?
Strong access controls play a major role improving ERP security by regulating and limiting access to confidential data and functionalities inside a system. Implementing robust access controls helps businesses to ensure that only their authorized personnel can view, modify, or interact with sensitive information.
3. Why is encryption crucial for ERP security?
Encryption is essential for ERP security as it offers an extra layer of protection for sensitive data stored and transmitted inside the system. Through data encryption, organizations can arrange it in an unreadable format, making it unclear for unauthorized users, even if they intercept. This helps to check unauthorized access and data breaches.
4. Why is employee training essential for ERP security?
Employee training is necessary to ensure ERP security as human error remains one of the major reasons for security breaches. Educating staff about staff protocols , practices and potential threats helps organizations to empower them to make informed decisions.
5. How can organizations check the effectiveness of their ERP security measures?
Companies can assess the effectiveness of their ERP security measures via regular security audits, penetration testings, and vulnerability assessments. These processes help to detect possible weaknesses and gaps in the ERP system’s security posture, enabling companies to make corrective measures and keep their ERP data safe from cyber threats.
Do You Require a Cloud ERP Software That Provides Real-time Insights?
Get in touch with the experts of ROCKEYE.
Request a Call
